- Home
- Azure
- Apps on Azure Blog
- How to connect Azure Key Vault from Python App Service using managed identity
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
In this blog, we will explore how to securely access Azure Key Vault from a Python App Service using managed identity. This method enhances security by avoiding the need to store credentials in code or configuration files. If you are interested in connecting to an Azure SQL database from a Python Function App using managed identity, you can find a related post here.
Azure Key Vault is a cloud service that provides a secure store for secrets, keys, and certificates. With managed identities for Azure resources, you can authenticate to services that support Microsoft Entra ID without needing credentials in your code.
Let's dive into the steps to achieve this with a Python App Service.
Steps:
-
Create a Python App Service in Azure:
Start by creating a Python App Service from the Azure portal. Ensure that you select a runtime that supports Python and configure your app as needed.
-
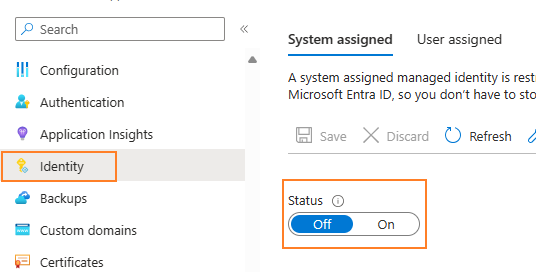
Enable Managed Identity:
In the Azure portal, navigate to your App Service and enable a system-assigned managed identity. This action will create an identity in Azure AD that is tied to your App Service.
You can also use an user-assigned managed identity which had been created in advance. Make sure to add a new app setting named "AZURE_CLIENT_ID" with value Client ID copied from selected user-assigned identity as required, Otherwise, you'll get error "Unable to load the proper Managed Identity."
-
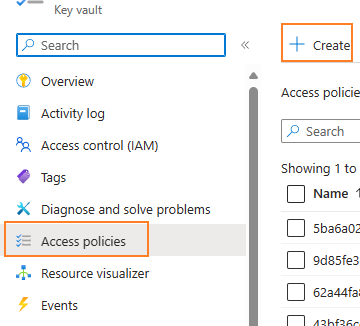
Grant Access to Azure Key Vault:
Once the managed identity is enabled, you need to grant it access to your Key Vault. In the Key Vault settings, add a new access policy and select the App Service's managed identity as the principal. Assign the necessary permissions (e.g., get, list, set secrets). If you are using RBAC(Role based access control) mode, grant necessary role assignments.
-
Install Required Python Packages:
To interact with secrets in Azure Key Vault, you'll need to install the
azure-keyvault-secretsandazure-identitypackages. You can do this by adding them in requirements.txt file, if you need to interactive with the certificates, add azure-keyvault-certificates.azure-keyvault-secrets
azure-identity -
Write the Python Code:
In your App Service, write Python code to authenticate with Azure Key Vault using the managed identity and retrieve secrets/certificates. Here's a sample snippet:
from azure.identity import DefaultAzureCredential from azure.keyvault.secrets import SecretClient KEY_VAULT_URL = "https://<YourKeyVaultName>.vault.azure.net/" credential = DefaultAzureCredential() # Get secret from Azure Key Vault secret_name = "test" secret_client = SecretClient(vault_url=KEY_VAULT_URL, credential=credential) retrieved_secret = secret_client.get_secret(secret_name) print(f"The secret value is: {retrieved_secret.value}") # Similarily, get certificate from Azure Key Vault certificate_client = CertificateClient(vault_url=KEY_VAULT_URL, credential=credential) certificate_name = "test" certificate = certificate_client.get_certificate(certificate_name) print("Certificate Name:", certificate.name) print("Certificate Value:", certificate.cer)This code uses the
DefaultAzureCredentialclass, which automatically uses the managed identity when running in Azure, and falls back to other authentication methods when running locally. The complete demo of Azure Function App can be found here. - Deploy to Azure App Service and verify the result.
Workflow:
- The App Service with a managed identity sends a request to Azure Key Vault using the identity's token.
- Azure Key Vault verifies the token and checks the permissions of the managed identity.
- If the managed identity has the appropriate permissions, the request is authorized, and the secret is retrieved.
By following these steps, you can securely access Azure Key Vault from your Python App Service with managed identity. This approach not only simplifies the authentication process but also significantly improves the security of your application by eliminating the need to manage credentials.
Stay tuned for more in-depth tutorials and feel free to reach out if you have any questions or comments.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.