- Home
- Azure
- Apps on Azure Blog
- Use Image Integrity to secure your AKS deployment
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Azure Kubernetes Service (AKS) now supports Image Integrity in public preview.
Containers are popular for cloud native application development and have increasingly become the common target for software supply chain attacks. Thus, delivering tools to help secure containerized software supply chains has been a growing call of AKS customers.
Digital signatures provide a way for software consumers to ensure the integrity and authenticity of the containers deployed. Image signing has become one of the most popular solutions to the aforementioned concern. The signed container images enable users to ensure deployments are built from a trusted entity and verify that those images haven't been tampered with since their creation.
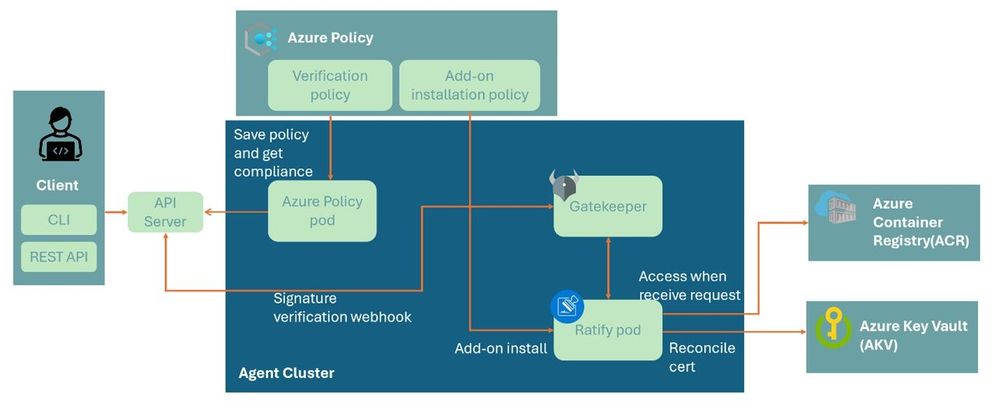
Image Integrity works by extending the CNCF project OPA Gatekeeper using another project Ratify, which expose image signature verification data to Gatekeeper so that policy can be applied to deployment images using that data. Together, these projects power the Image Integrity feature on AKS.
The tech stack powering Image Integrity
We at Microsoft have embraced a culture of contributing to and working with the OSS community, with a particular focus on the CNCF and cloud native projects. In line with this, we have been collaborating on two open-source projects: Ratify and OPA Gatekeeper and have committed to building experiences that leverage these projects. Microsoft continues to shape future releases from our customer learnings through project contributions and open sourcing the components designed to improve container supply chain security.
The technical stack that enables the image signature verification on AKS and the basic scaffolding to add an admission control policy to the AKS container offering is based on the following key components:
Azure Policy and OPA Gatekeeper
Azure Policy extends Gatekeeper, an admission controller webhook for Open Policy Agent (OPA), to apply at-scale enforcements and safeguards on your clusters in a centralized, consistent manner. Azure Policy makes it possible to manage and report on the compliance state of your Kubernetes clusters at-scale from one centralized policy assignment.
To enable the Image Integrity signature verification scenario, Azure Policy’s Add-On for AKS newly extends Gatekeeper’s external data capability. Allow you to make context-aware authorization and policy decisions by injecting external data that describes what is happening in the world and then writing policy using that data.
Ratify
Ratify is a verification engine as a binary executable and on Kubernetes which enables verification of artifact security metadata and admits for deployment only those that comply with policies you create.
Ratify extends Gatekeeper by providing additional verification evidence to the Gatekeeper. This can be signature, attestation, and potentially any other supply chain information you want to validate in order to secure deployment.
Image signature verification policy on AKS
On AKS, we leverage Azure Policy to help enforce organizational standards and to assess compliance at-scale. Through applying substantial built-in policies, customers can easily enforce controls and achieve the desired security posture. We have been dedicated to contributing policies to Azure Policy’s built-in definition library that flag, enforce and remediate AKS configurations based on security best practices, regulatory requirements and customer demands.
Ensuring that only trusted container images are used is a key scenario of container supply chain security and extending the built-in AKS policies coverage to image signature verification scenario becomes a quick way for AKS customer to safeguard the deployment by using signed images.
How it works on AKS
To leverage Image Integrity to safeguard the deployment on your AKS cluster, follow these steps:
- Enable Image Integrity using built-in AKS policy initiative. It includes an enforcement policy that enables Image Integrity add-on and an admission control policy that verifies signatures.
- Set up the verification configurations through applying CRDs. You can define Ratify configs including verifiers, certificates in this step. The experience though is going to change when it comes to GA as we are looking to provide a more managed experience.
- Deploy the image the validate if the verification policy takes effect.
The deployment request shall be denied or get alerted if using untrusted images.
Looking ahead
We are excited to learn how this feature can enable industries like Finance, Communication, and SaaS/ISV Partners that are looking to meet regulatory requirements with Image Integrity on AKS. We look forward to continuing to innovate in the open-source space of supply chain security and make AKS the platform of choice to run your most sensitive workloads at scale. Start using Image Integrity following the guidance now.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.