- Home
- Azure
- Apps on Azure Blog
- Min TLS Cipher Suite (Preview) Now Available on Azure Portal and Info on Upcoming Changes Before GA
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
From a previous announcement on the Minimum TLS Cipher Suite (preview), the feature only supported the configuration through the API. The good news is that now users can configure the minimum TLS cipher suite for incoming requests through the Azure portal! This feature is currently only supported on Premium SKUs and above on multi-tenant App Service. This article will go through what cipher suites are and how they work on App Service, the minimum TLS cipher suite experience on Azure portal, and more information about an upcoming change that will happen before General Availability (GA).
What are cipher suites and how do they work on App Service?
A cipher suite is a set of instructions that contains algorithms and protocols to help secure network connections between clients and servers. By default, the front-end's OS would pick the most secure cipher suite that is supported by both App Service and the client. However, if the client only supports weak cipher suites, then the front-end's OS would end up picking a weak cipher suite that is supported by them both. If your organization has restrictions on what cipher suites should not be allowed, you may update your web app’s minimum TLS cipher suite property to ensure that the weak cipher suites would be disabled for your web app.
Azure Portal Experience
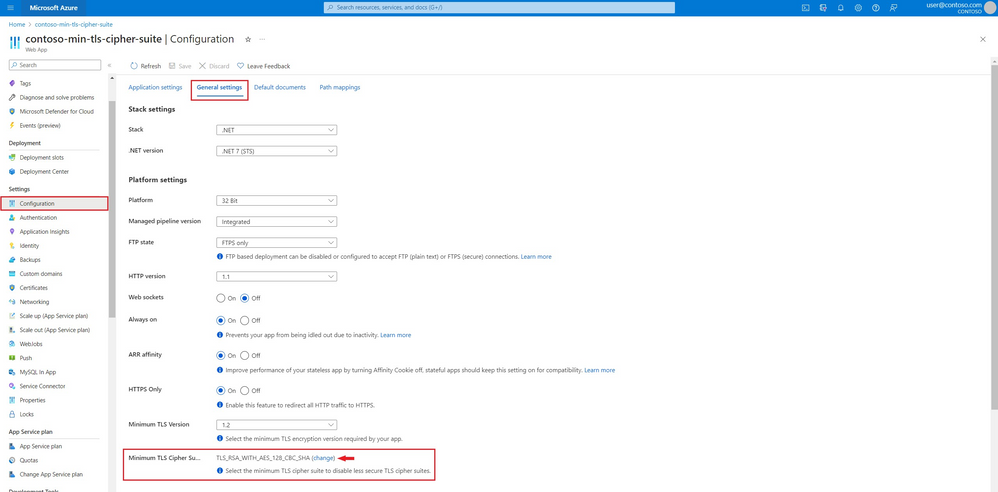
You can find this feature in your resource overview page under “Configuration” > “General settings” > “Min TLS Cipher Suite (preview)”. Click on “change” to configure your minimum TLS cipher suite.
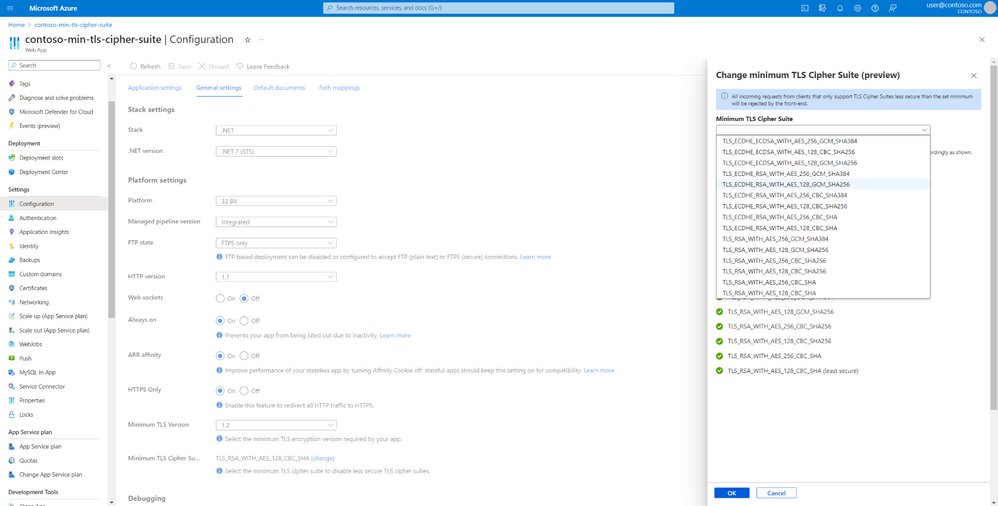
A right pane will pop up and will show you the list of TLS cipher suites that are currently supported by our front-ends and information on what TLS cipher suites are enabled/disabled for the web app. For the default experience, all TLS cipher suites will be enabled for the web app.
To configure a minimum TLS cipher suite, select a TLS cipher suite from the dropdown that you would like to configure as the minimum for the site.
Once you selected a minimum TLS cipher suite, you will see a change in the original list reflecting what TLS cipher suites will be enabled/disabled based on your selection. To save the configuration, you need to click on “Ok” at the bottom of the right pane and then click on “Save” from the Configuration blade. Clicking on “Ok” alone will not update your minimum TLS cipher suite!
What’s Next?
A very popular question that comes up is “When is this feature going to hit General Availability (GA)?”. We are currently targeting sometime at the end of the calendar year for GA, but there is a change coming before it. The current list of TLS cipher suites will be updated where there will be a change in the TLS cipher suite priority order. We would like to ensure that this priority order change happens during the Preview stage to guarantee stability for the feature when it hits GA. While the list of supported cipher suites along with its priority order may still be updated later, we don’t expect this to happen frequently. We are estimating this upcoming change of cipher suite priority order to happen sometime in the second semester of this calendar year. We will be providing more information/announcements once we have a more specific timelines to share at least a month before the update.
To prepare your services for the change, you can refer to the lists below on the current TLS cipher suite priority ordering and the to-be updated priority ordering set for later this year.
Current TLS Cipher Suite Priority Order
- TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256
- TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
- TLS_RSA_WITH_AES_256_GCM_SHA384
- TLS_RSA_WITH_AES_128_GCM_SHA256
- TLS_RSA_WITH_AES_256_CBC_SHA256
- TLS_RSA_WITH_AES_128_CBC_SHA256
- TLS_RSA_WITH_AES_256_CBC_SHA
- TLS_RSA_WITH_AES_128_CBC_SHA
To-Be Updated TLS Cipher Suite Priority Order
ETA for this change to happen is sometime in the latter half of this year’s semester. We will be providing more information/announcement once we have more specific timelines to share.
- TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
- TLS_RSA_WITH_AES_256_GCM_SHA384
- TLS_RSA_WITH_AES_128_GCM_SHA256
- TLS_RSA_WITH_AES_256_CBC_SHA256
- TLS_RSA_WITH_AES_128_CBC_SHA256
- TLS_RSA_WITH_AES_256_CBC_SHA
- TLS_RSA_WITH_AES_128_CBC_SHA
Understanding Impact of Update
The new ordering of TLS cipher suites is based on the TLS Cipher Suites in Windows 2022. The main change that’s happening is that the “TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256” is moving to a lower priority. Despite the change with the ordering, the front-end's OS would still pick the most secure cipher suite that is supported by both App Service and the client. In general, we expect this change to be a non-issue for almost all customers. If your clients have a hard dependency on a specific TLS cipher suite being chosen, you may want to review this as soon as possible.
Depending on your app’s configured minimum TLS cipher suite, your app might end up disabling “TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256” cipher suite (#2 from current list; #5 from updated list) after the change. As an example, if your app’s current configured minimum is set to “TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256” (#5 from current list; #4 from updated list), currently your web app will allow client requests that uses “TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256”. However, after the update, your app will no longer allow client requests that uses that cipher suite as it is then considered to be less secure than the set minimum.
If you selected “TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256” TLS cipher suite (#2 from current list; #5 from updated list) as the minimum, your app would end up enabling more TLS cipher suites after this change. As an example, if your current minimum is set to the said TLS cipher suite, your web app will allow client requests that uses either of the top two TLS cipher suites from the current list. After the update, your web app will allow client requests that uses one of the top five TLS cipher suites from the updated list.
We currently do not have a more specific timeline to share. However, we will be providing more information regarding the dates and timeframe of when the change is expected to happen at least a month before the update.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.