- Home
- Azure
- Azure Integration Services Blog
- Connecting Integration Account to Azure KeyVault behind Firewall.
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
In the Integration account when trying to add a private certificate to use it in workflows, a private key is needed.
And adding private key from Azure KeyVault having public access, can be done as mentioned in the document : Add certificates to secure B2B messages in workflows - Azure Logic Apps | Microsoft Learn
Current Scenario addressed in this Document:
- Adding Private Certificate to Integration account and the private key is in KeyVault.
- The KeyVault is behind Firewall with Network restriction.
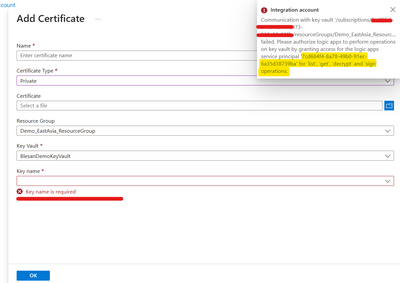
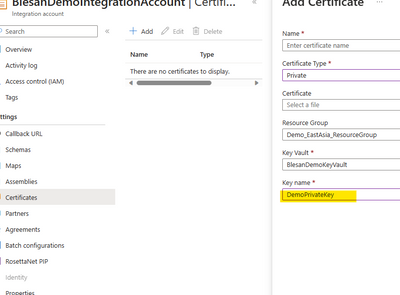
Trying to add a private Certificate in the integration account, will produce the below error when selecting the private key.
(Communication with key vault '/subscriptions/SUBSCRIPTION-ID/resourceGroups/RESOURCEGROUPNAME/providers/Microsoft.KeyVault/vaults/KEYVAULTNAME' failed. Please authorize logic apps to perform operations on key vault by granting access for the logic apps service principal '7cd684f4-8a78-49b0-91ec-6a35d38739ba' for 'list', 'get', 'decrypt' and 'sign' operations.)
The error message requires Logic apps Service principle to have list, get, decrypt and sign operation permissions over the KeyVault.
For that, there are 2 ways of granting access to logic apps service principle based on the access configuration as mentioned below:
Granting Access to Logic Apps Service Principle on Azure KeyVault:
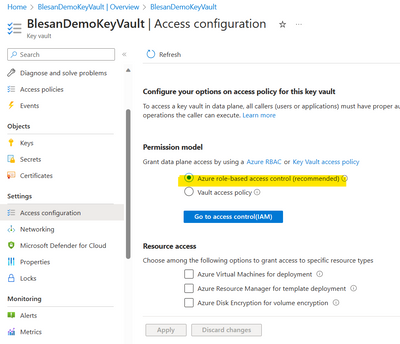
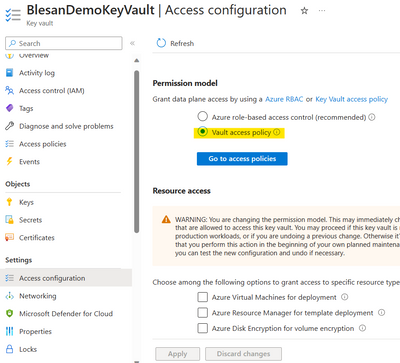
1. If your KeyVault's Access configuration is 'Azure-Role based Access Control'.
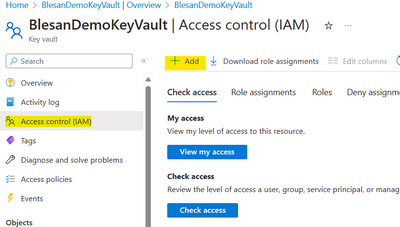
Then you can add the access to your logic app by going to the Access control Tab and Add role,
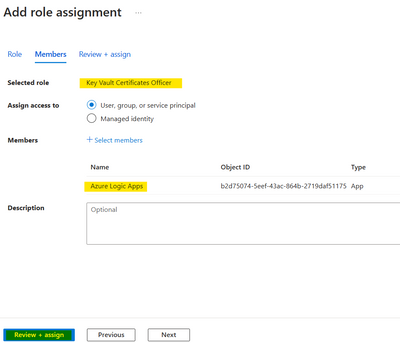
Adding the role 'Key Vault Certificate Office' is sufficient for the azure logic apps as shown below
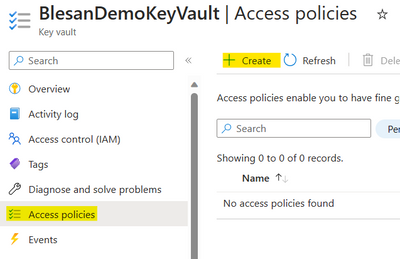
2. If the KeyVault's access configuration is 'Vault Access Policy'
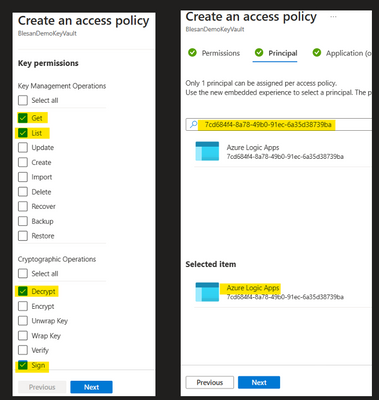
Then you can add the access to the logic apps by navigating to the access policy and adding a new access policy
and adding the List, Get, Decrypt and Sign access to the logic apps service principle '7cd684f4-8a78-49b0-91ec-6a35d38739ba'
The above performed actions would be sufficient to get the private key in the integration account when adding a private certificate if the KeyVault has public access with no firewall.
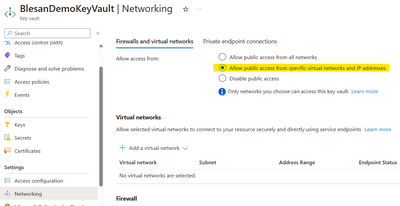
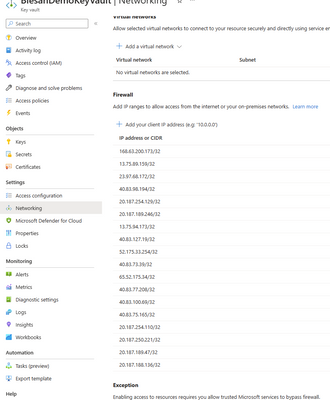
However, in our scenario we have a KeyVault with Firewall Enabled and restricted access as shown below. With this restriction we still get the same error as shown in the first screenshot.
KeyVault with Firewall enabled:
Now, to successfully add the certificate with private key, we need to whitelist the Inbound and Outbound IP address of the Logic apps specific to a region in the KeyVault Firewall, where the region is based on the Azure region of the Integration account.
Inbound and Outbound IP address for logic app based on the azure region can be found here: Limits and configuration reference guide - Azure Logic Apps | Microsoft Learn
Reason to whitelist Logic app IP address of the same region as Integration account is that the Integration account uses Consumption(Multi-tenant) Logic apps Runtime in background for processing/handling requests.
After successfully adding the in/out bound IP address of logic apps, we can add the private certificate in the integration account with private key in KeyVault with Firewall without any error.
Below is one example:
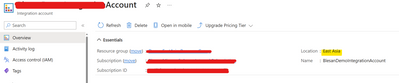
Integration account with region as EastAsia:
So, whitelisted the EastAsia Ip address of the logic apps based on the integration account azure region:
Then we will be able to successfully add the private key from KeyVault behind firewall after following the steps mentioned in the above section "Granting Access to Logic Apps Service Principle on Azure KeyVault":
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.