- Home
- Azure
- Apps on Azure Blog
- Unable to access Webapp or Kudu site hosted in ILB ASE
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
The Azure App Service Environment is a deployment of Azure App Service into a subnet in an Azure virtual network (VNet). There are two ways to deploy an App Service Environment (ASE):
- With a VIP on an external IP address, often called an External ASE.
- With a VIP on an internal IP address, often called an ILB ASE because the internal endpoint is an internal load balancer (ILB).
You can read more about ILB App Service Environment here v2 , v3 .
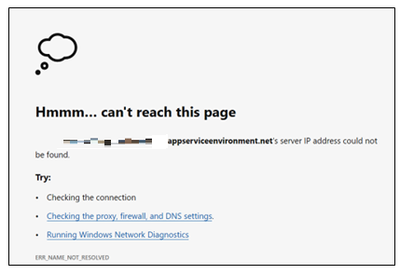
When accessing Site / Kudu Site hosted in ILB ASE, you might encounter error as below where the site is unreachable. There can be multiple factors due to which the site can’t be accessible:
- DNS Server is not mapped correctly to App Service / Vnet.
- DNS Records are not created.
- Private DNS Zone is not created .
- Private DNS Zone is not linked with the Virtual Network where the ASE is created.
- NSG rules or Firewall can be blocking the traffic.
Below are troubleshooting steps:
It is essential that your machine must be able to resolve to both the App Service / Function App hostname and SCM site. If site doesn’t resolve, then you would see similar error as below:
1. To check if the name-resolution is returning the correct ILB ASE IP , you can execute the below commands from the machine you are trying to connect to the site:
|
nslookup <AppName>.<ASEName>.appserviceenvironment.net |
Execute this command from the VM / Machine which is in the Virtual Network or Connected network. |
|
Resolve-DNSName <AppName>.<ASEName>.appserviceenvironment.net |
Powershell command to check name resolution. |
The commands should provide you the ILB IP mapped to this domain if the DNS records are configured properly. If not, then you would need to update the DNS Configuration accordingly. You can refer this document for DNS Configuration.
2. You can execute below commands to check the connectivity to the apps in ILB ASE:
|
curl -v <AppName>.<ASEName>.appserviceenvironment.net net -k |
Execute this command from the VM / Machine which is in the Virtual Network or Connected network. |
|
test-netconnection <AppName>.<ASEName>.appserviceenvironment.net -port 443 |
PowerShell Command to check connectivity. |
3. Install PSPing in the Virtual Machine from where you are trying to access the app service as this will help us to make a TCP call to the ILB IP to check the connectivity.
PsPing implements Ping functionality, TCP ping, latency and bandwidth measurement. To download PSPing utility click here.
|
psping <URL>: <Port> |
Note: If the connectivity fails, check if there are any Network Security Groups (NSG) mapped to the subnet of ASE or Virtual Machine / NIC which could be blocking the traffic.
- ASEv2: If you have ASEv2 , you can verify in the NSG if the below rules are present to allow the application traffic for port 80,443.
- ASEv3: You should ensure that Azure Load Balancer is able to connect to the subnet on port 80. This port is used for health checks of the internal virtual machine.
|
Source / Destination Port(s) |
Direction |
Source |
Destination |
|
* / 80 |
Inbound |
AzureLoadBalancer |
App Service Environment subnet range |
|
* / 80,443 |
Inbound |
VirtualNetwork |
App Service Environment subnet range |
4. For testing purpose ( Not recommended for Production workloads) , you can choose to update the hosts file entry:
- Windows : Hosts file location : C:\Windows\System32\drivers\etc\hosts
|
ILB IP |
Host File Entry |
Purpose |
|
<ILB IP> |
*.<asename>.appserviceenvironment.net |
This record is used for resolving Site URL. |
|
<ILB IP> |
*.scm.<asename>.appserviceenvironment.net |
This record is used for resolving Kudu site URL. |
|
<ILB IP> |
<asename>.appserviceenvironment.net |
This record is used for SSO to Kudu/scm site. |
- Linux : You can create similar records in resolv.conf file:
5. You can go to Azure Portal > Diagnose and Solve Problems and view the detectors: Vnet Verifer.
This detector will help to verify the required NSG considerations are being met or not for the ASE.
More Information:
ASE v3: App Service Environment networking - Azure App Service Environment | Microsoft Learn
ASE v2: Networking considerations - Azure App Service Environment | Microsoft Learn
If you have any other questions, feel free to comment below!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.